Active Directory (AD) is Microsoft's proprietary directory service. It runs on Windows Server & enables admins to manage permissions and access to network resources. Active Directory stores data as objects.
An Object is a single element, such as a user, group, application, or device such as a printer.
[Working] Active Directory
Active Directory (AD) is Microsoft's proprietary directory service. It runs on Windows Server and enables administrators to manage permissions and access to network resources.
Active Directory stores data as objects. An object is a single element, such as a user, group, application, or device such as a printer. Objects are normally defined as either resource, such as printers or computers, or security principals, such as users or groups.
Active Directory categorizes directory objects by name and attributes. For example, the name of a user might include the name string, along with information associated with the user, such as passwords and Secure Shell keys.
The main service in Active Directory is Domain Services (AD DS), which stores directory information and handles the interaction of the user with the domain. AD DS verifies access when a user signs into a device or attempts to connect to a server over a network. AD DS controls which users have access to each resource, as well as group policies.
Other Microsoft and Windows operating system (OS) products, such as Exchange Server and SharePoint Server, rely on AD DS to provide resource access. The server that hosts AD DS is the domain controller.
Features in Active Directory Domain Services
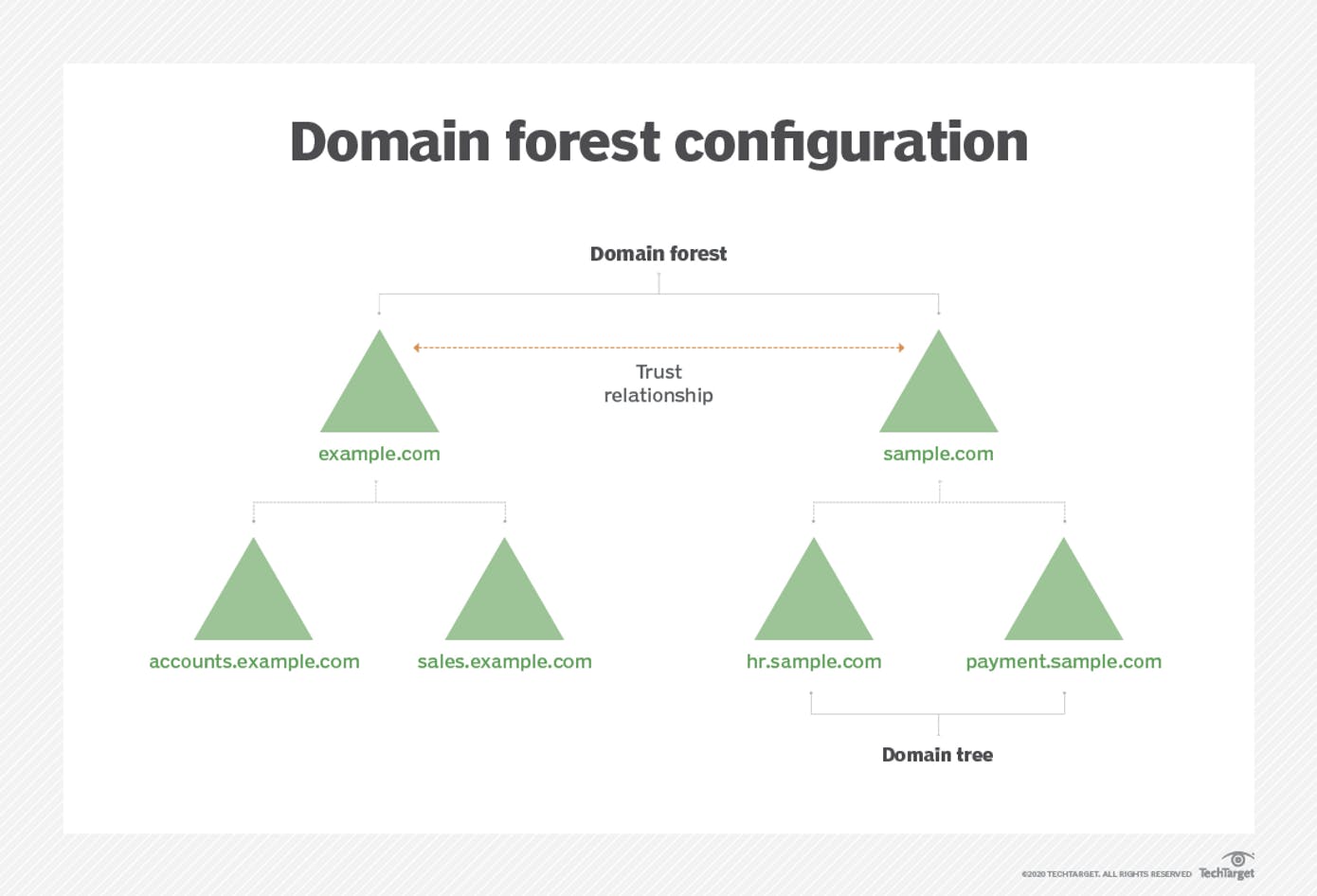
Active Directory Domain Services uses a tiered layout structure consisting of domains, trees, and forests to coordinate networked elements.
Domains are the smallest of the main tiers, while forests are the largest. Different objects, such as users and devices, that share the same database will be on the same domain. A tree is one or more domains grouped together with hierarchical trust relationships. A forest is a group of multiple trees. Forests provide security boundaries, while domains -- which share a common database -- can be managed for settings such as authentication and encryption.
A domain is a group of objects, such as users or devices, that share the same AD database. Domains have a domain name system
A tree is one or more domains grouped together. The tree structure uses a contiguous namespace to gather the collection of domains in a logical hierarchy. Trees can be viewed as trust relationships where a secure connection, or trust, is shared between two domains. Multiple domains can be trusted where one domain can trust a second, and the second domain can trust a third. Because of the hierarchical nature of this setup, the first domain can implicitly trust the third domain without needing explicit trust.
A forest is a group of multiple trees. A forest consists of shared catalogs, directory schemas, application information, and domain configurations. The schema defines an object's class and attributes in a forest. In addition, global catalog servers provide a listing of all the objects in a forest. According to Microsoft, the forest is Active Directory's security boundary.
Organizational Units (OUs) organize users, groups, and devices. Each domain can contain its own OU. However, OUs cannot have separate namespaces, as each user or object in a domain must be unique. For example, a user account with the same username cannot be created.
Containers are similar to OUs, but Group Policy Objects cannot be applied or linked to container objects.
Active Directory services
Lightweight Directory Services has the same codebase as AD DS, sharing similar functionalities, such as the application program interface. AD LDS, however, can run in multiple instances on one server and holds directory data in a data store using Lightweight Directory Access Protocol.
Lightweight Directory Access Protocol is an application protocol used to access and maintain directory services over a network. LDAP stores objects, such as usernames and passwords, in directory services, such as Active Directory, and shares that object data across the network.
Certificate Services generates, manages, and shares certificates. A certificate uses encryption to enable a user to exchange information over the internet securely with a public key.
Active Directory Federation Services authenticates user access to multiple applications -- even on different networks -- using single sign-on (SSO). As the name indicates, SSO only requires the user to sign on once, rather than use multiple dedicated authentication keys for each service.
Rights Management Services control information rights and management. AD RMS encrypts the content, such as email or Microsoft Word documents, on a server to limit access.
[Pricing Model] - Active Directory
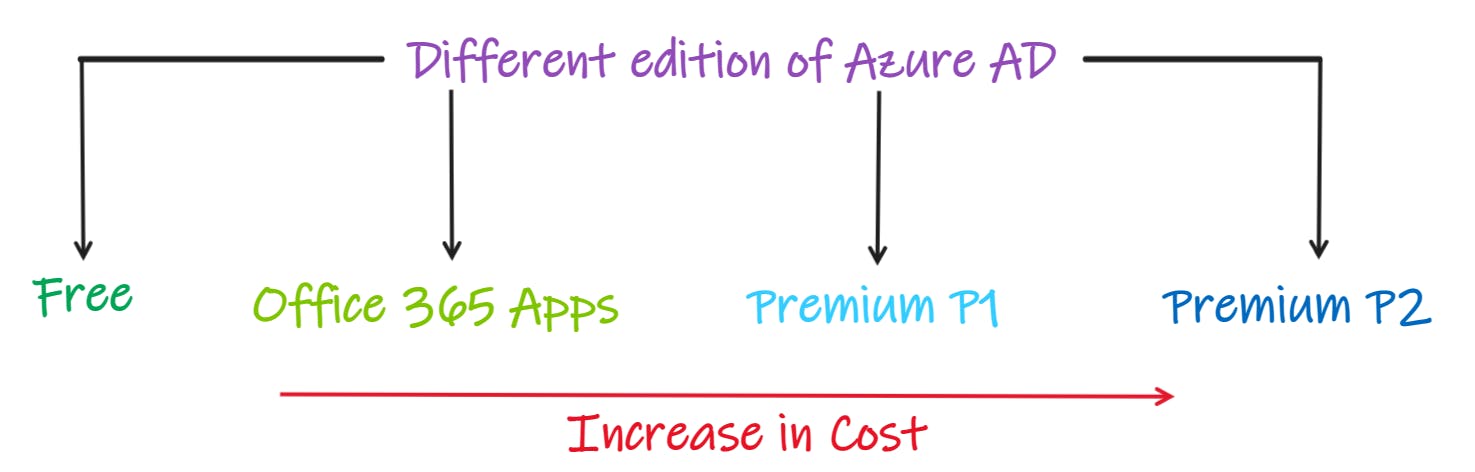
Free - Provides user & group management, on-premises directory sync, basic reports, self-service password change for cloud users, and SSO Azure, M365.
Office 365 Apps - Office 365 subscriptions include the free editions, but Office 365 E1, E3, E5, F1 & F3 subscriptions.
Premium P1 - In addition to the free features, P1 also lets your hybrid users across both on-premises and cloud resources. It also supports advanced admin, such as dynamic groups, self-service group management, Microsoft Identity Manager & cloud write-back capabilities, which allow self-service password reset for your on-prem users.
Premium P2 - In addition to Free & P1 Features, P2 also offers Azure Active Directory Identity Protection to help provides risk-based Conditional Access to your apps & critical company data and privileged identity management & monitor admin and their access to resources and provide just-in-time access when needed.
Additional - [Trusting Terminology]
Active Directory relies on trusts to moderate the access rights of resources between domains. There are several different types of trusts:
A one-way trust is when a first domain allows access privileges to users on a second domain. However, the second domain does not allow access to users on the first domain.
A two-way trust is when there are two domains and each domain enables access to users of the other domain.
A trusted domain is a single domain that enables user access to another domain, which is called the trusting domain.
A transitive trust can extend beyond two domains and allow access to other trusted domains within a forest.
An intransitive trust is a one-way trust that is limited to two domains.
An explicit trust is a one-way, nontransitive trust that is created by a network admin.
A cross-link trust is a type of explicit trust. Cross-link trusts take place between domains within
- the same tree, with no child-parent relationship between the two domains, or
- different trees.
A forest trust applies to domains within the entire forest and can be one-way, two-way, or transitive.
A shortcut joins two domains that belong to separate trees. Shortcuts can be one-way, two-way, or transitive.
A realm is a trust that is transitive, intransitive, one-way, or two-way.
An external trust is a trust that links domains across separate forests or domains that are non-AD. External trusts can be nontransitive, one-way, or two-way.
A private access management (PAM) trust is a one-way trust that is created by Microsoft Identity Manager between a production forest and a bastion forest.
Reference

